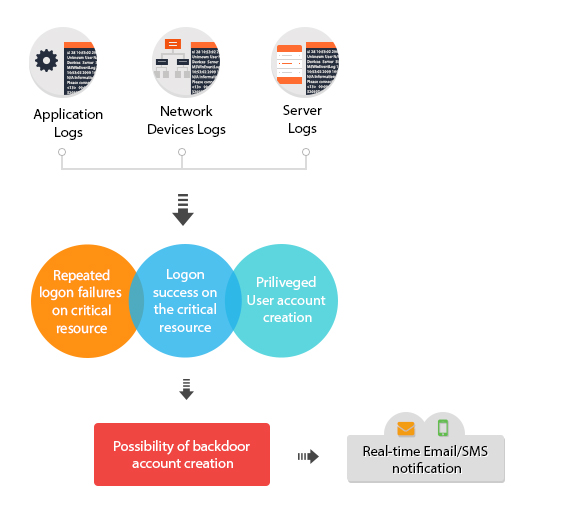
 Real-time event correlation is all about proactively dealing with threats. Data breaches are on вҖӢthe rise and hackers use highly targeted attacks to intrude upon enterprise networks and steal sensitive data. Protecting your network data from attackers involves detecting security threats at its early stage. Security investigators need to determine whether a suspicious event or chain of security events that had happened on the network is a potential security threat or not.
Real-time event correlation is all about proactively dealing with threats. Data breaches are on вҖӢthe rise and hackers use highly targeted attacks to intrude upon enterprise networks and steal sensitive data. Protecting your network data from attackers involves detecting security threats at its early stage. Security investigators need to determine whether a suspicious event or chain of security events that had happened on the network is a potential security threat or not.Manually investigating events across the network from various log sources and correlating them to formulate an attack pattern will be a herculean task for the security investigators.
To effortlessly identify the possible intrusions in the network, you need to have an automated effective correlation engine that gives a complete scope of any security incident by building relationships between events happening across your network infrastructure.
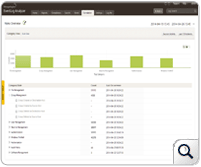 вҖӢEventLog Analyzer's correlation engine effectively connects security incidents from a wide array of log sources in your network. It comes bundled with over 70 out-of-the-box correlation rules that cover user access, user logins, file integrity, user creation, group policies, unintended software installations and more. With this out-of-the-box correlation rules IT security professionals can detect and identify anomalies as and when they happen without any hassles of manual intervention.
вҖӢEventLog Analyzer's correlation engine effectively connects security incidents from a wide array of log sources in your network. It comes bundled with over 70 out-of-the-box correlation rules that cover user access, user logins, file integrity, user creation, group policies, unintended software installations and more. With this out-of-the-box correlation rules IT security professionals can detect and identify anomalies as and when they happen without any hassles of manual intervention.The IT security professionals are notified in real time during any threshold violations or network anomalies by an SMS or email.
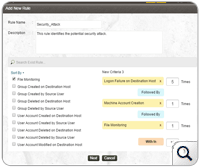 EventLog Analyzer's correlation rule builder can baseline the 'normal' network behavioral patterns by specifying the levels for each individual correlation rules.It allows you to create attack patterns that are prone to occur at your вҖӢnetwork infrastructure with its simple easy to use interface. All you have do is drag and drop the predefined rules to formulate attack patterns.
EventLog Analyzer's correlation rule builder can baseline the 'normal' network behavioral patterns by specifying the levels for each individual correlation rules.It allows you to create attack patterns that are prone to occur at your вҖӢnetwork infrastructure with its simple easy to use interface. All you have do is drag and drop the predefined rules to formulate attack patterns.Once the rule is formulated, the correlation engine analyzes & correlates the logs collected across your network based on the set of defined rules, looks for a significant symptom that can lead to a potential attack and alerts you in real-time via email or SMS and hence you can proactively react to the breach.
The correlation engine,