EventLog Analyzer includes alerts on event logs which notify administrators when an event matching a specific criteria is generated. Alerting helps administrators monitor critical servers and processes on the network without spending too much time watching graphs and reports.
EventLog Analyzer comes with another versatile feature, real-time event correlation and instant alert notifications. You can configure alerts to correlate events based on threshold conditions or anomalous events and notify in real-time for any threshold violations or network anomalies. You can get instant notification via email and SMS. You can also execute a custom script or program upon alert generation and take quick remedial action to secure your network assets
You can define which hosts or group of hosts need to be monitored. Depending on the size of your enterprise, critical processes may run on a single dedicated server, or be spread out over a group of servers. EventLog Analyzer lets you set up alerts for events generated in both cases.
If you need to trigger an alert based on events generated with a specific log type, log message, or severity, you can define a custom alert profile to notify administrators.
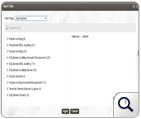 EventLog Analyzer includes 500+ predefined alert criteria for Windows, Linux, Unix, Applications, and Networking devices. These predefined alert criteria are meticulously drafted and grouped so as to eliminate the need to create a user-defined alert pattern for regular activities.The вҖӢвҖӢ alert criteria also reduce the time for setting up an alert profile thus increasing the security administrator's operational efficiency.
EventLog Analyzer includes 500+ predefined alert criteria for Windows, Linux, Unix, Applications, and Networking devices. These predefined alert criteria are meticulously drafted and grouped so as to eliminate the need to create a user-defined alert pattern for regular activities.The вҖӢвҖӢ alert criteria also reduce the time for setting up an alert profile thus increasing the security administrator's operational efficiency.
If you need to trigger an alert based on specific type of compliance violation for HIPAA, GLBA, PCI, or SOX, based on failed logon attempts, policy changes, account changes, and audit logs cleared, you can define a compliance alert profile to notify administrators.
EventLog Analyzer supports a variety of alert notifications.